Target: Get the status of Antivirus Windows Defender or any other 3rd party Antivirus software via “Run a Script” from ConfigMgr into a Log-File.
In the WMI namespace “root\SecurityCenter2” you find the list of installed Antivirus products and their status. I created two scripts to detect the status of Windows Defender and one for Sophos Antivirus. The scripts will show clients where either Windows Defender or Sophos Antivirus is in no clean status or not up to date.
The Scripts converts the product state to an hex-value and outputs the clients with an non-compliant Antivirus into an log file which can be opened with cmtrace.exe or MS Excel.
Windows Defender needs an Hex-Code of 061100 if it’s enabled and up to date.
The following hex-states can occur for Windows Defender:
Windows Defender
060100= disabled and up2date
061110 = enabled and outdated
061100 = enabled and up2date
Sophos Antivirus needs a an Hex-Code of 051000 if it’s enabled and up to date.
Prerequisites: Create a UNC-share and provide everyone full-access in additional modify the NTFS-Permission to provide “Domain Computers” at least write permission on the folder.
Here you can find the script for Windows Defender copy the script and follow the steps below:
The script for Sophos Antivirus is at the end of that blog post.
#currentdate
$CuDate = Get-Date
$CuDate.ToUniversalTime()
#generate random sleep time between 1-10 milliseconds
$rdom= Get-Random -Maximum 10
#logdestination
$destination = "\\servername\sharename$\AvInfo_Defender_SCCM.log"
#get Antivirus
$avWMIres = get-wmiobject -namespace root\SecurityCenter2 -computername localhost -Query "Select * from AntiVirusProduct" | where {$_.Displayname -eq "Windows Defender"}
if ($avWMIres -eq $null)
{
#create the Log and save
Start-Sleep -Milliseconds $rdom
$Log = $env:COMPUTERNAME + "; " + "no Windows Defender found" + "; " + "0" + "; " + $CuDate
$Log | Out-File -FilePath $aFilePath -append -Force
}
else
{
foreach ($av in $avWMIres)
{
#Defender enabled and up to date has a hex state of 061100
#Windows Defender
#(060100) = disabled and u2d
#(061110) = enabled and not u2d
#(061100) = enabled and u2d
$tohex = [Convert]::ToString($av.productState, 16)
#add zero for hex
$tohex = "0" + $tohex
$successavstate = "061100"
#if not good AV is installed -> add to LOG
If ($tohex -ne $successavstate)
{
#create the Log and save
Start-Sleep -Milliseconds $rdom
$Log = $env:COMPUTERNAME + "; " + $av.displayName + "; " + $tohex + "; " + $CuDate
$Log | Out-File -FilePath $destination -append -Force
}
}
}
Open the ConfigMgr console and navigate to \Software Library\Overview\Scripts
Select Create Script:
Paste the script with your modified UNC-Share Path:
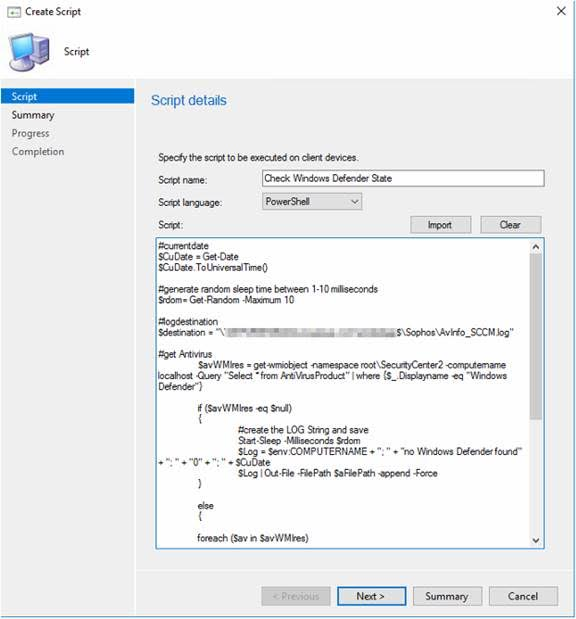
Save the Script:

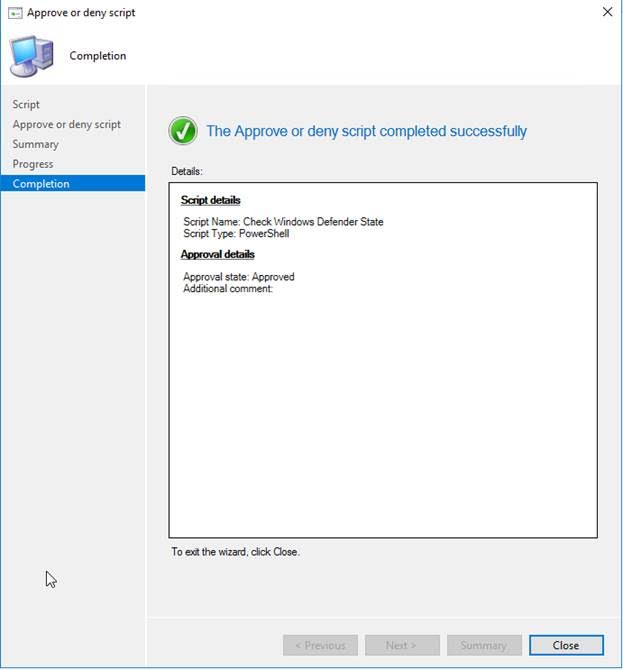
Approve the Script:


Run the Script against the required device collection:

Check the result in the log / in my case all clients have a disabled Microsoft Defender and they are up to date. As we are using Sophos Antivirus the result is as expected:

You can modify the script to check also the state of your 3rd party Antivirus Software. Here you can find the script for Sophos:
#currentdate
$CuDate = Get-Date
$CuDate.ToUniversalTime()
#generate random sleep time between 1-10 milliseconds
$rdom = Get-Random -Maximum 10
#logdestination
$destination = "\\servername\sharename$\AvInfo_Sophos_SCCM.log"
#get Antivirus
$avWMIres = get-wmiobject -namespace root\SecurityCenter2 -computername localhost -Query "Select * from AntiVirusProduct" | where { $_.displayName -eq "Sophos Anti-Virus" }
if ($avWMIres -eq $null)
{
#create the Log and save
Start-Sleep -Milliseconds $rdom
$Log = $env:COMPUTERNAME + "; " + "no Sophos found" + "; " + "0" + "; " + $CuDate
$Log | Out-File -FilePath $aFilePath -append -Force
}
else
{
foreach ($av in $avWMIres)
{
#Sophos enabled and up to date has a hex state of 051000
#Windows Defender
#05 = AV installed
#10 = Active
#00 = u2d
$tohex = [Convert]::ToString($av.productState, 16)
#add zero for hex
$tohex = "0" + $tohex
$successavstate = "051000"
#if not good AV is installed -> add to LOG
If ($tohex -ne $successavstate)
{
#create the Log and save
Start-Sleep -Milliseconds $rdom
$Log = $env:COMPUTERNAME + "; " + $av.displayName + "; " + $tohex + "; " + $CuDate
$Log | Out-File -FilePath $destination -append -Force
}
}
}
The result in the Logs looks like the following. In my case I have a few Clients where Sophos is not up to date and the Antivirus-Team needs to check the clients:

